Application-Level Linux Firewall OpenSnitch 1.3.0 Adds A Process Details Dialog, GUI RPM Packages
OpenSnitch, an application-level firewall for Linux, has been updated to version 1.3.0 which adds a process details dialog, RPM GUI packages, and more.
Opensnitch monitors outbound connections that your applications are trying to make, preventing or permitting their connection based on a set of rules (the user is prompted to allow or deny access when no existing rules are found). The application is inspired by Little Snitch, a commercial host-based application firewall for macOS. It's made of a daemon written in Go, and a PyQt5 GUI.
The original OpenSnitch developer mentioned back in June 2019, that they are not working on this program anymore, so the project was forked (I wrote about that here). Recently though, Gustavo Iñiguez Goia, the fork developer, appears to have gotten control of the main OpenSnitch GitHub repository, releasing the latest 1.3.0 version there.
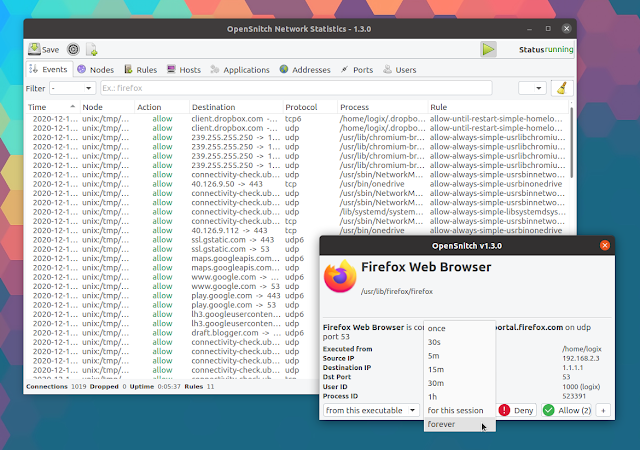
But back to OpenSnitch 1.3.0. The biggest new feature in this release is the addition of a process details dialog. It shows a process status (with used memory, pid, and much more), open files, I/O statistics, mapped memory files, stack, and environment variables.
This can be accessed by going to the Applications tab, double-clicking on an item (in the "what" column), and finally clicking on the computer icon to the left of the executable path:
You might also like: 3 Ways Of Installing Tor Browser On Linux (Ubuntu, Fedora, openSUSE, Etc.)
Also, with this release, there are OpenSnitch GUI RPM packages available for download. Previously, only the OpenSnitch daemon was packaged as RPM. Thanks to this, OpenSnitch is easier to install on RPM-based Linux distributions like Fedora, openSUSE, CentOS, etc.
Other changes in OpenSnitch 3.0:
- Allow adding system rules. You can now configure iptables rules by editing the file /etc/opensnitchd/system-fw.json. OpenSnitch will ensure that the rules you have configured there are not deleted from the system
- Allow filtering connections by destination network
- daemon: fixed ftrace and auditd monitor method
- daemon: fixed error when IPv6 is not enabled in the system / IPv6 handling
- daemon: improved application rules checking
- ui: fallback to Qt built-in icons if no valid icon theme is configured
- ui: fixed compatibility with python3.9
Download OpenSnitch
The OpenSnitch releases page has DEB (Debian, Ubuntu, Linux Mint, Pop!_OS, etc.) and RPM (Fedora, CentOS, openSUSE, etc.) binaries for both the daemon and the GUI. Install them both if you want to use this on your desktop.
OpenSnitch is also available on AUR, as stable or git packages for Arch Linux / Manjaro.
Gnome Shell users will need an extension like the Ubuntu AppIndicators extension (this is installed by default on Ubuntu) to be able to access the OpenSnitch tray icon.