OpenSnitch Linux Application Firewall Fork With Improvements And Bug Fixes
OpenSnitch, an application firewall for Linux, is no longer under active development. This didn't mean it was the end for this project though, because Gustavo forked it about 8 months ago, and has been constantly improving it since.
OpenSnitch (fork) is a free an open source application-level firewall for Linux that's made of a daemon (written in Go) and a GUI (PyQt5). It monitors outbound connections that your applications are trying to make, preventing or permitting their connection based on a set of rules (the user is prompted to allow or deny access when no existing rules are found). The application is inspired by Little Snitch, a commercial host-based application firewall for macOS.
It's worth noting from the start that just like the original OpenSnitch firewall software, the fork is work in progress, with its page saying to "do not expect it to be bug free and do not rely on it for any type of security", without going into any details.
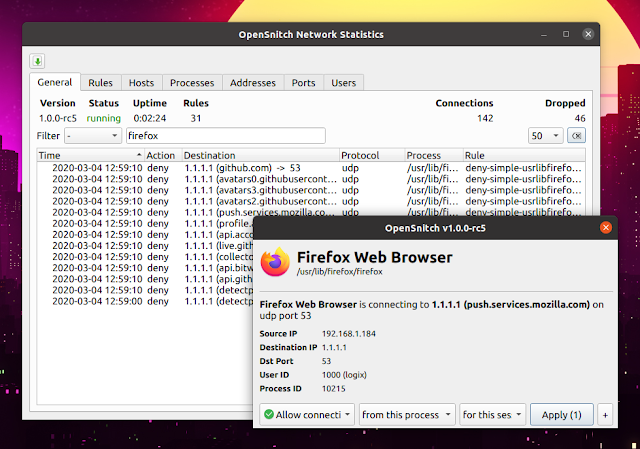
Let's take a look at how this application works. Having the OpenSnitch daemon running in the background, and the OpenSnitch tray UI running, when an application tries to access the Internet a dialog prompt is shown asking if you want to allow or deny connections from this process (or port, etc.), once, for a number of seconds / minutes, this session or forever.
This dialog contains information like the application name, domain name / IP it's trying to connect to, port, source IP, destination IP and port, user ID and process ID.
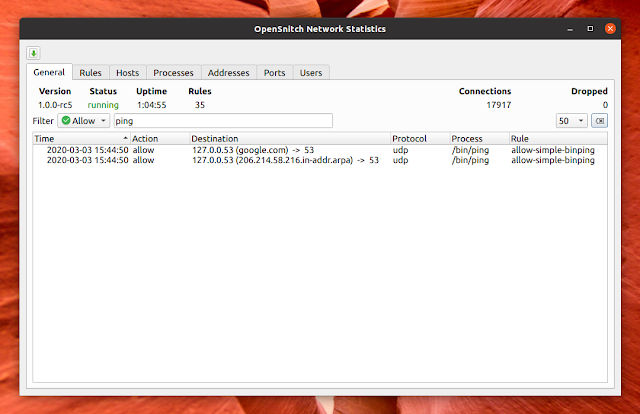
The tray icon allows access to the OpenSnitch Network Statistics (there's also a button to save the statistics to a .cvs file):
This GUI doesn't allow changing the OpenSnitch rules, so after you've allowed or denied access for some processes / applications, you'll no longer be able to change that using a GUI. Until the OpenSnith GUI gets supports for editing existing firewall rules (or manually adding rules from the GUI), you'll need to edit the rule files, which can be found in
This is an example of a simple OpenSnitch rule:
You might also like: bandwhich Shows What`s Taking Up Your Network Bandwidth On Linux And macOS
Since forking OpenSnitch, Gustavo has improved the software and fixed many issues, including:
Besides this, there are now OpenSnitch DEB binaries for download, making it easy to install this firewall software on Debian 9 and newer, Ubuntu 16.04 and newer, and Linux Mint 18 and newer, along with other Linux distributions based on these (e.g. Pop!_OS, etc.).
You might like: How To Permanently Change The MAC Address On Linux
The OpenSnitch fork developer has made OpenSnitch DEB packages available for download (you need to download and install both
[Later edit] For Arch Linux / Manjaro users, the AUR opensnitch-git package was switched from the old, unmaintained OpenSnitch to the fork, so you can use that to install it.
For installing OpenSnitch (fork) from source please see its documentation.
OpenSnitch (fork) is a free an open source application-level firewall for Linux that's made of a daemon (written in Go) and a GUI (PyQt5). It monitors outbound connections that your applications are trying to make, preventing or permitting their connection based on a set of rules (the user is prompted to allow or deny access when no existing rules are found). The application is inspired by Little Snitch, a commercial host-based application firewall for macOS.
It's worth noting from the start that just like the original OpenSnitch firewall software, the fork is work in progress, with its page saying to "do not expect it to be bug free and do not rely on it for any type of security", without going into any details.
Using OpenSnitch application-level firewall on Linux
Let's take a look at how this application works. Having the OpenSnitch daemon running in the background, and the OpenSnitch tray UI running, when an application tries to access the Internet a dialog prompt is shown asking if you want to allow or deny connections from this process (or port, etc.), once, for a number of seconds / minutes, this session or forever.
This dialog contains information like the application name, domain name / IP it's trying to connect to, port, source IP, destination IP and port, user ID and process ID.
The tray icon allows access to the OpenSnitch Network Statistics (there's also a button to save the statistics to a .cvs file):
This GUI doesn't allow changing the OpenSnitch rules, so after you've allowed or denied access for some processes / applications, you'll no longer be able to change that using a GUI. Until the OpenSnith GUI gets supports for editing existing firewall rules (or manually adding rules from the GUI), you'll need to edit the rule files, which can be found in
/etc/opensnitchd/rules/ This is an example of a simple OpenSnitch rule:
$ cat /etc/opensnitchd/rules/allow-simple-usrlibfirefoxfirefox.json
{
"created": "2020-02-24T14:16:23.5976661+02:00",
"updated": "2020-02-24T14:16:23.597682816+02:00",
"name": "allow-simple-usrlibfirefoxfirefox",
"enabled": true,
"action": "allow",
"duration": "always",
"operator": {
"type": "simple",
"operand": "process.path",
"data": "/usr/lib/firefox/firefox",
"list": []
}You might also like: bandwhich Shows What`s Taking Up Your Network Bandwidth On Linux And macOS
OpenSnitch fork
Since forking OpenSnitch, Gustavo has improved the software and fixed many issues, including:
- Added support for advanced rules (lists), which can be used to allow or restrict connections based on destination IP, port and more - screenshot above
- The Network Statistics UI has been greatly improved, now allowing you to filter results and configure the number of items to show on the General tab, and more. It's now also possible to view details of a rule/process from General tab
- Improved UI performance and fixed UI freezing in some cases, an issue that was quite common for users of the old OpenSnitch firewall
- UI HiDPI fixes
- Added more time frames to the allow/deny dialog (30s, 5m, 15m, 30m, 1h)
- It's possible to use ftrace (debugfs) or /proc to search for running proccessess (PIDs) and obtain the process path
- If the daemon can't communicate with the UI, the default action is applied
- Added option to allow/deny second level domains
- Fixed crashes occuring when parsing .desktop files (an issue quite common in the old OpenSnitch)
- Added UI alerts to warn about unanswered connections
- Display the app window when there's no system tray available
- Intercept and parse UDPLite connections
- Allow intercepting localhost and multicast connections
- Other changes
Besides this, there are now OpenSnitch DEB binaries for download, making it easy to install this firewall software on Debian 9 and newer, Ubuntu 16.04 and newer, and Linux Mint 18 and newer, along with other Linux distributions based on these (e.g. Pop!_OS, etc.).
You might like: How To Permanently Change The MAC Address On Linux
Download OpenSnitch (fork)
The OpenSnitch fork developer has made OpenSnitch DEB packages available for download (you need to download and install both
opensnitch and python3-opensnitch-ui DEB packages), along with the source code. The OpenSnitch firewall daemon starts automatically after installing the DEB packages, but you'll need to start the GUI (tray) manually from your applications menu. The OpenSnitch tray icon will automatically start the next time you login.[Later edit] For Arch Linux / Manjaro users, the AUR opensnitch-git package was switched from the old, unmaintained OpenSnitch to the fork, so you can use that to install it.
For installing OpenSnitch (fork) from source please see its documentation.