apt-key Is Deprecated. How To Add OpenPGP Repository Signing Keys Without It On Debian, Ubuntu, Linux Mint, Pop!_OS, Etc.
This article explains how to securely add OpenPGP keys and third-party APT repositories on Debian, Ubuntu, and Linux distributions based on these, like Linux Mint, Pop!_OS, Elementary OS and so on, to replace the deprecated apt-key.
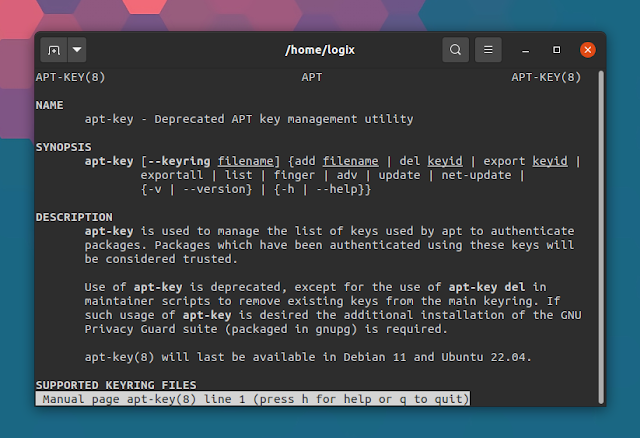
When you try to add an APT repository key using apt-key on Debian, Ubuntu and Linux distributions based on these, you'll see the following message: "Warning: apt-key is deprecated. Manage keyring files in trusted.gpg.d instead (see apt-key(8))". Some newer Ubuntu versions also show a warning when using a deprecated key: "W: (...) Key is stored in legacy trusted.gpg keyring (/etc/apt/trusted.gpg), see the DEPRECATION section in apt-key(8) for details".
The apt-key man page mentions that the "use of apt-key is deprecated, except for the use of apt-key del in maintainer scripts to remove existing keys from the main keyring". What's more, "apt-key will last be available in Debian 11 and Ubuntu 22.04."
The reason for this change is that when adding an OpenPGP key that's used to sign an APT repository to /etc/apt/trusted.gpg or /etc/apt/trusted.gpg.d, the key is unconditionally trusted by APT on all other repositories configured on the system that don't have a signed-by (see below) option, even the official Debian / Ubuntu repositories. As a result, any unofficial APT repository which has its signing key added to /etc/apt/trusted.gpg or /etc/apt/trusted.gpg.d can replace any package on the system. So this change was made for security reasons (your security).
It's also worth noting that while the apt-key deprecation message says to "manage keyring files in trusted.gpg.d instead", the Debian wiki states otherwise. That's because adding OpenPGP keys to /etc/apt/trusted.gpg and /etc/apt/trusted.gpg.d is equally unsecure, as mentioned above.
You can continue to use apt-key for now as it still works. However, it would be a good idea to start transitioning to utilizing the signed-by option as explained below, especially if you maintain a third-party repository.
So what's the proper, secure way of adding third-party (unofficial) repositories and their OpenPGP signing keys on Debian, Ubuntu, and Linux distributions based on these, like Linux Mint, Pop!_OS, Elementary OS and so on, to replace the deprecated apt-key?
1. Download the APT repository key
According to the Debian wiki, the key should be downloaded over HTTPS to a location only writable by root, for example /usr/share/keyrings. The key name should contain a short name describing the repository, followed by archive-keyring. E.g. if the repository is called myrepository, the key file should be named myrepository-archive-keyring.gpg.
The OpenPGP key file can be ascii-armored or not. To verify if a key file is ascii-armored, download the key file and run this command (note that the key extension can be .gpg, .asc, .key, and probably others):
file <repo-key>.gpgIf the output of this command is similar to the following, then the key is ascii-armored:
repo-key.gpg: PGP public key block Public-Key (old)That being said, this is how to properly, and securely download and add a repository signing key to your system:
- For ascii-armored OpenPGP keys
To download using wget and add such an OpenPGP key to your system, use:
wget -O- <https://example.com/key/repo-key.gpg> | gpg --dearmor | sudo tee /usr/share/keyrings/<myrepository>-archive-keyring.gpgWhat everything in this command does / means:
wgetdownloads the key fromhttps://example.com/key/repo-key.gpgand outputs the key to stdout (-O-). Replace the URL here with the URL of the key you want to download and add to your systemgpg --dearmor: thegpgcommand is the OpenPGP encryption and signing tool; its--dearmoroption unpacks the input from an OpenPGP ASCII armorsudo tee /usr/share/keyrings/<myrepository>-archive-keyring.gpg: as super user (sudo), read the standard input, which in this case is the output provided bygpg --dearmor, and write this to the/usr/share/keyrings/<myrepository>-archive-keyring.gpgfile. Replace the<myrepository>name with a descriptive name for the repository key you're adding
For example, to add the Signal application APT repository, you'd use:
wget -O- https://updates.signal.org/desktop/apt/keys.asc | gpg --dearmor | sudo tee /usr/share/keyrings/signal-archive-keyring.gpgOr to use the command given as an example on the Debian wiki (you need to run it as root, e.g. after running sudo -i; it uses curl instead of wget to download the key):
curl <https://example.com/key/repo-key.gpg> | gpg --dearmor > /usr/share/keyrings/<myrepository>-archive-keyring.gpgExample of using this command to add the Signal APT repository:
curl https://updates.signal.org/desktop/apt/keys.asc | gpg --dearmor > /usr/share/keyrings/signal-archive-keyring.gpg- For non-ascii-armored OpenPGP keys
Download the OpenPGP key using wget and add it to your system using:
wget -O- <https://example.com/key/repo-key.gpg> | sudo tee /usr/share/keyrings/<myrepository-archive-keyring.gpg>Or to use the command given as an example on the Debian wiki (you need to run it as root, e.g. after running sudo -i):
wget -O /usr/share/keyrings/<myrepository-archive-keyring.gpg> <https://example.com/key/repo-key.gpg>I did not add an example here because I couldn't find a third-party repository that uses a non ascii-armored OpenPGP key.
- To import OpenPGP keys directly from a keyserver to a file in
/usr/share/keyrings:
sudo gpg --no-default-keyring --keyring /usr/share/keyrings/<myrepository>-archive-keyring.gpg --keyserver <hkp://keyserver.ubuntu.com:80> --recv-keys <fingerprint>Instead of hkp://keyserver.ubuntu.com:80, you can use some other key server if you wish.
Example in which we'll import the OpenPGP key of the Linux Uprising Shutter PPA to /usr/share/keyrings/linux-uprising-shutter-archive-keyring.gpg (the fingerprint can be obtained by clicking the green "Technical details about this PPA" link from the PPA page - it's under "Adding this PPA to your system"):
sudo gpg --no-default-keyring --keyring /usr/share/keyrings/linux-uprising-shutter-archive-keyring.gpg --keyserver hkp://keyserver.ubuntu.com:80 --recv-keys 1CC3D16E460A94EE17FE581CEA8CACC073C3DB2AYou might also like: How To Keep A Package From Updating In Ubuntu, Debian Or Linux Mint [APT]
2. Add the repository sources.list entry
Third-party repository sources.list entries should be added in the /etc/apt/sources.list.d directory, and not directly in the /etc/apt/sources.list file.
Previously, a sources.list file from the /etc/apt/sources.list.d directory would look like this:
deb https://repository.example.com/debian/ stable mainHowever, to be able to use the key added under step 1, the sources.list entry must now look like this (/etc/apt/sources.list.d/<myrepository.list>):
deb [signed-by=/usr/share/keyrings/<myrepository>-archive-keyring.gpg] <https://repository.example.com/debian/ stable main>It's important to note here that if you also want to add the arch=amd64 option together with signed-by, you need to separate the two options by a space, like this:
deb [arch=amd64 signed-by=/usr/share/keyrings/<myrepository>-archive-keyring.gpg] <https://repository.example.com/debian/ stable main>As an example, to add the Signal repository to your Debian / Ubuntu system, create a file (as root; for example to open Nano command line text editor with this file: sudo nano /etc/apt/sources.list.d/signal.list) called signal.list in /etc/apt/sources.list.d with the following contents (assuming you've already downloaded the key as explained above, as /usr/share/keyrings/signal-archive-keyring.gpg):
deb [arch=amd64 signed-by=/usr/share/keyrings/signal-archive-keyring.gpg] https://updates.signal.org/desktop/apt xenial mainRemember to run sudo apt update after adding a new signing key and repository, to update the software sources.
You may also add the repository in the Deb822 file format, but to try and not complicate things even more, I won't explain that here. You can read about that on the Debian wiki.
You may also like: How To Find The Package That Provides A File (Installed Or Not) On Ubuntu, Debian Or Linux Mint
How to remove an already existing OpenPGP key added to the APT trusted keyring (/etc/apt/trusted.gpg or /etc/apt/trusted.gpg.d)
When adding OpenGPG keys as explained above, you'll want to remove the same key from /etc/apt/trusted.gpg or /etc/apt/trusted.gpg.d, in case you've added it there previously. Without doing this, there's no added security benefit.
Removing existing OpenPGP keys from the /etc/apt/trusted.gpg.d directory should be pretty easy. That's because the key filename should be pretty descriptive. For example, the Tor repository gpg key filename from this directory on my system is deb.torproject.org-keyring.gpg
So to get rid of already existing keys added to /etc/apt/trusted.gpg.d, all you have to do is remove the key files. You need to do this as root. So either open the file manager of your choice as root, using admin:// (for example, to open a location as root in Nautilus, press Ctrl + L so you can type in its address bar, and type admin:///etc/apt/trusted.gpg.d), or remove them from the command line, using:
sudo rm /etc/apt/trusted.gpg.d/<myrepository-keyring.gpg>The instructions below also work for removing keys from the /etc/apt/trusted.gpg.d directory.
As for removing APT gpg keys stored in /etc/apt/trusted.gpg, things are a bit more complicated. Use the following command to list all APT OpenPGP keys imported in both /etc/apt/trusted.gpg and /etc/apt/trusted.gpg.d:
apt-key listThe keys stored in /etc/apt/trusted.gpg should be listed at the top, followed by the keys from the /etc/apt/trusted.gpg.d directory. You'll need to inspect the key uid in order to figure out the key that you want to remove. Usually, the uid should show the company or user that signed the key, followed by their email address.
Keys from /etc/apt/trusted.gpg are listed by apt-key list like this (example):
pub rsa4096 2016-04-22 [SC]
B9F8 D658 297A F3EF C18D 5CDF A2F6 83C5 2980 AECF
uid [ unknown] Oracle Corporation (VirtualBox archive signing key) <info@virtualbox.org>
sub rsa4096 2016-04-22 [E]
The key ID is the last 8 characters of the GPG key's fingerprint (so in this example, that's 2980AECF).
To delete a key (from either /etc/apt/trusted.gpg or /etc/apt/trusted.gpg.d), you can now use:
sudo apt-key del <KEY-ID>For example, to delete the key from the example above, you'd use:
sudo apt-key del 2980AECFYou might like: How To List All Packages In A Repository On Ubuntu, Debian Or Linux Mint [APT]
References:
- https://wiki.debian.org/DebianRepository/UseThirdParty
- https://askubuntu.com/a/1307181/1149075
- https://zebnemeth.wordpress.com/2021/01/15/install-signal-desktop-using-gpg/
- https://github.com/docker/docker.github.io/issues/11625
Thanks to u/ZebNemeth for the suggestion!